Securing your cloud infrastructure – start with the basics – first 10 things to get right
As a certified solutions architect, I work with our clients across a number of industries to help navigate the difficulties of securing their cloud computing infrastructure. No matter if it’s working with a hybrid cloud, public cloud deployments, or private cloud, the security issue continues to persist. We work hands on to protect their infrastructure from the overload of possible threats.
Let’s walk through 10 key, but basic steps that you can take to secure your cloud computing infrastructure.
1. Strengthen Authentication with MFA
MFA is the best way to protect accounts from unwanted accessibility. This should always be done on your IAM and root user accounts. If you have single sign- on enabled to assist with account management, you can enforce MFA there to prevent reuse of stolen credentials. If you implement MFA at the federated identity provider (IdP), you are able to take advantage of the existing MFA processes in your organization.
2. Implement and Validate IAM roles using best practices
Having individuals each assigned a unique identity greatly increases the security of your cloud infrastructure. This is also important to do for applications and objects in your environment. Using your cloud’s identity and access management tool, create policies that restrict access based upon time of day, length of access, geolocation and other criteria. Additionally, it is a good practice to limit administrative users to changing cloud components within their specific scope of responsibility. It is best to avoid the use of shared administrative accounts to maintain accountability.
3. Encrypt sensitive information
Utilize your cloud platform’s encryption solution. Amazon Web services has Amazon EBS, which is a simple encryption solution that doesn’t require you to build, maintain, and secure your own key management infrastructure for your EBS resources. The encryption takes place on the servers hosting EC2 instances and ensures the security of both data-in-transit and data-in-rest and its attached EBS storage. With Amazon EBS encryption, you can encrypt both the data volumes and boot of an EC2 instance.
4. Keep Certificates Up-to-Date
When it comes to cloud security, it is important to keep your SSL/TLS certificates updated. As time passes, older versions of the certificate may not be compatible with your cloud services. This will typically lead to errors for custom applications, impacting the overall security and productivity of your company.
5. Use Security Groups
Security Groups act as a virtual firewall, allowing you to control inbound and outbound traffic. It is important to utilize security groups for the security of you infrastructure and to limit access to administrative services and databases. It is also important to monitor and delete security groups that are not being used and to audit them periodically.
6. Configure a Password Policy
Utilizing a strong password policy is critical for the security of your organization.
A good password policy describes a set of conditions for password creation, modification, and deletion. For example, enforce multi-factor authentication (mentioned above), automated lockout after multiple failed login attempts, or a password renewal policy after a certain period of time (for example 60 days). Good password policies can significantly reduce the chances of a security breach.
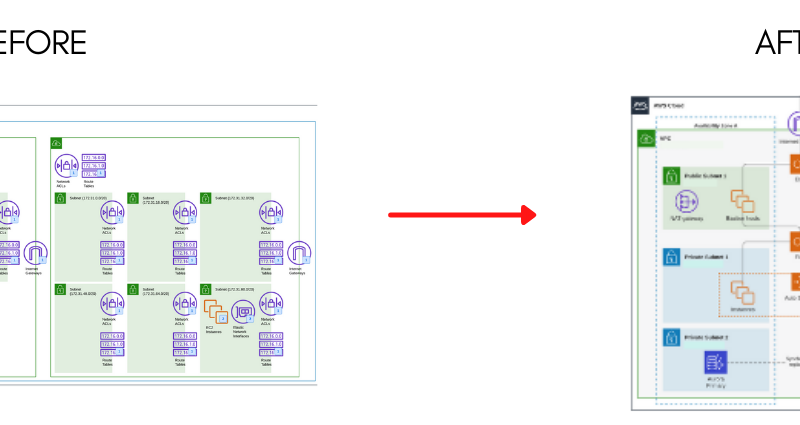
7. Use a VPC if Your Infrastructure has more than one server
8. Stop instances that are not in use
Scheduling your instances to stop during the times that are not in use not only saves you money on your cloud bill, but also provides added security and protection. Leaving servers and databases on all of the time gives time for someone to try to break in and connect to servers within your infrastructure. This particularly occurs during off-hours when you don’t have as many eyes on your IT. By setting a schedule for the servers to be off, you minimize the opportunity for outside attacks on those servers.
9. Log and Monitor
Logging and monitoring are important parts of a well developed security plan. Being able to investigate unexpected changes in your environment or perform analysis to iterate on your security posture relies on having access to data. It is a good idea to write logs to a bucket designated for logging. The logs should be encrypted at rest and permissions should prevent deletion of the logs.
10. Take Actions on Findings
Turn on services that provide you with action item for findings on your account. You have to take action when you see findings. The action(s) to take are determined by your own incident response policy. For each finding, ensure that you have determined what your required response actions should be.